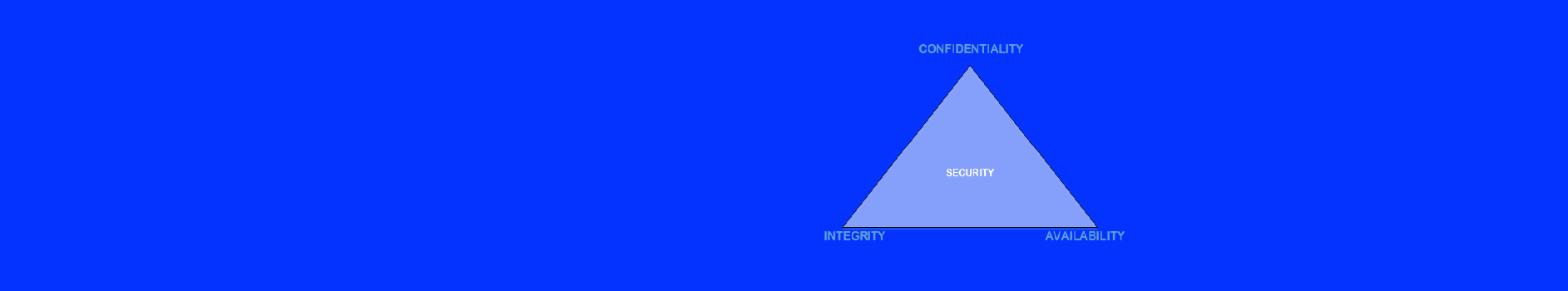
Identify
- Asset Management
- Business Environment
- Governance
- Risk Assessment
- Risk Management Strategy

Protect
- Access Control
- Awareness & Training
- Data Security
- Info Protection Process & Procedures
- Maintenance
- Protective Technology

Detect
- Anomalies & Events
- Security Continuous Monitoring
- Detection Processes

Respond
- Response Planning
- Communications
- Analysis
- Mitigation
- Improvements
Recover
- Recovery Planning
- Improvements
- Communications